7 Ways Your Personal Information Gets Exposed Online
Introduction – The Hidden Leaks in Everyday Life
Most people imagine data breaches as dramatic hacks, but the reality is subtler and more constant. Every online action, from downloading an app to sharing a photo, can leave a digital trail that advertisers, data brokers, or criminals can follow. Your personal information doesn’t need to be stolen in one big attack; it can leak drip by drip through daily habits.
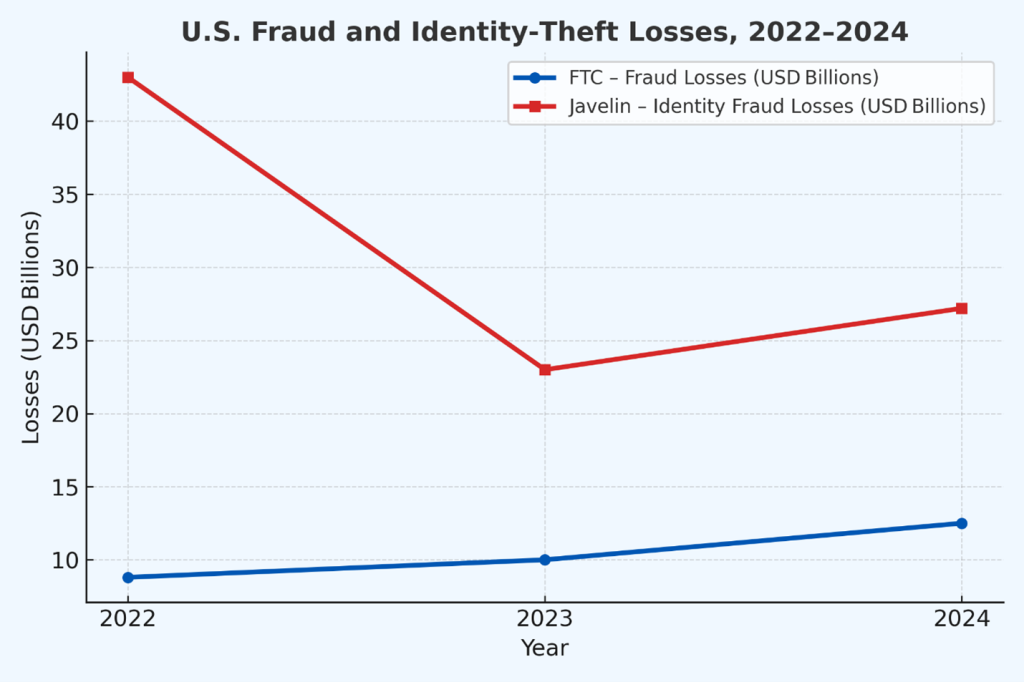
Exposures don’t just threaten privacy, they increase risks of fraud, harassment, or identity theft. According to Experian, in 2024, U.S. fraud and identity-theft losses topped US $12.7 billion[AdF1] with about 1.1 million identity-theft reports and 2.6 million fraud cases.
This article explores seven common routes through which your information escapes into the public sphere. The goal is not to alarm, but to make you aware, so you can seal the leaks before they spread.
For a full overview of how exposure fits into family-level data protection, see: Digital Identity Protection and PII Removal: Why It’s Now a Family Essential.
1. Oversharing on Social Media and Public Platforms
It starts innocently enough: a birthday post, a graduation photo, a “check-in” at a favorite café. Each share can reveal small pieces of personally identifiable information (PII), your location, relationships, age, routines, or even travel patterns. When combined, these details can form a comprehensive digital profile.
Cybersecurity firm Kaspersky reports that almost half of respondents of a recent survey (47%) admit to sharing personal or sensitive information online, increasing their risk of data leaks, identity theft, and cyber-exploitation. Photos of driver’s licenses, boarding passes, or work badges have all been used in scams. Even closed “friends-only” networks are vulnerable; screenshots and third-party apps can resurface private data elsewhere.
Oversharing isn’t limited to individuals. Family members may inadvertently post children’s full names or addresses, exposing minors to privacy risks. Professionals often post workplace milestones without realizing their employer’s internal systems or badges appear in the background.
To understand what qualifies as PII and why small details matter, read What Is PII and Why Does It Matter? (Beginner’s Guide).
For best practices on reducing oversharing and strengthening family data awareness, see Protecting Your Family from Identity Theft: Best Practices.
2. Corporate Data Breaches and Misconfigured Databases
Sometimes, you can do everything right, and still get exposed. The largest leaks often result from breaches in corporate databases or cloud storage systems. In 2024 alone, IBM Security estimated the average cost of a data breach at $4.88 million , with compromised personal data accounting for nearly half of all incidents.
Top 5 Largest U.S.-Linked Data Breaches (Since 2020)
| Date | Company | Records (Compromised) |
|---|---|---|
| Apr 2024 | National Public Data (U.S. data broker) | ≈ 2,900,000,000 |
| Feb 2024 | UnitedHealth / Change Healthcare | ≈ 190,000,000 |
| Apr 2024 | AT&T | ≈ 109,000,000 |
| Aug 2021 | T‑Mobile (U.S.) | ≈ 76,600,000 |
| Apr 2021 | Facebook (Meta) | ≈ 533,000,000 |
Human error plays a huge role. Misconfigured cloud servers, weak employee passwords, and delayed software updates give cybercriminals easy entry points. When attackers penetrate corporate systems, they rarely target one person, they target millions.
Two recent examples illustrate the scale: HR data was present in 82% of reported breaches in 2025, revealing payroll and Social Security details; and credit-reporting giant TransUnion confirmed a breach affecting 4.5 million U.S. customers. Such events show how institutions we trust with our most private data can become weak links.
Even after a company announces a breach, leaked data often resurfaces on dark-web marketplaces for years.
For detailed guidance on removing exposed information from these public and private databases, see How to Remove Personal Information from Data Broker Websites.
3. The Expanding Risk from Smart Devices (IoT Leaks)
Your refrigerator, security camera, car, or smartwatch may know more about you than your friends do. The “Internet of Things” (IoT) connects billions of devices that continuously collect and transmit data, often without strong encryption or clear consent
A 2025 report by Statista estimated over 17 billion connected devices worldwide, generating immense volumes of personal information, from voice commands to movement patterns. Weak or default passwords remain one of the most exploited vulnerabilities. Attackers can access baby monitors, fitness trackers, or home assistants to spy, record, or map your household routines.
Even anonymized IoT data can expose identity when cross-referenced with other sources. A fitness app leak, for example, once revealed military base locations through soldiers’ running routes.

The solution isn’t to abandon smart devices, it’s to manage them wisely: change default credentials, disable unnecessary data sharing, and regularly update firmware.
To explore the psychological benefits of taking back control of your digital life, read The Psychology of Peace of Mind.
4. Phishing Scams
Phishing remains one of the oldest—and most effective—ways cybercriminals steal personal information. Fraudsters send fake emails, texts, or phone calls that appear to come from legitimate organizations such as banks, delivery services, or even government agencies. These messages often urge quick action: “verify your account,” “confirm your password,” or “track your package.”

Once you click a fraudulent link or share personal details, attackers can gain access to email accounts, financial portals, or entire identity profiles. Verizon’s 2024 Data Breach Investigations Report found that 36% of all breaches involved phishing, often using social engineering techniques that exploit urgency or fear.
To protect yourself, verify sender addresses carefully, avoid clicking on suspicious links, and enable multi-factor authentication (MFA) wherever possible.
Learn more about protecting family members from online deception in Protecting Your Family from Identity Theft: Best Practices.
5. Public Wi-Fi Networks
Free Wi-Fi can be a trap. When you connect to an unsecured network in a café, airport, or hotel, your data may travel unencrypted—allowing nearby attackers to intercept it through what’s known as a “man-in-the-middle” attack. These cybercriminals can eavesdrop on your emails, hijack your sessions, or even inject malicious code into your browsing stream.
A 2025 Norton survey revealed that 54% of public Wi-Fi users access sensitive accounts (such as banking or health portals) without realizing the risk. Even legitimate networks can be spoofed by impostors with nearly identical names—one wrong click, and your data is theirs.
To stay safe, use a reputable VPN, avoid logging into financial accounts on public Wi-Fi, and turn off automatic network connections.
Read the Protecting Your Family from Identity Theft guide for practical network and device protection steps.
6. Malware and Spyware

Sometimes the greatest threats arrive disguised as something helpful—a document attachment, a free software update, or a link promising rewards. Clicking or downloading these files can install malware or spyware that silently tracks your keystrokes, passwords, and browsing history.
According to Microsoft’s 2025 Security Intelligence Report, one in every 14 email attachments carries a malicious payload. Spyware can capture screenshots, record audio, and even activate webcams, turning your own devices into surveillance tools. Many infections come not from hackers but from outdated software or pirated applications that lack proper security controls.
Avoid downloading files from unverified sources, keep antivirus software up to date, and enable automatic operating system patches.
For guidance on recognizing and removing personal data from malicious or compromised sources, explore How to Remove Personal Information from Data Broker Websites.
To understand why this vigilance matters legally and ethically, revisit What Is PII and Why Does It Matter? (Beginner’s Guide).
7. Data Broker Websites
Beyond hackers and scams lies a quieter, legal industry that trades in your information daily: data brokers. These companies scrape, compile, and sell details such as your address, age, purchasing history, and even predicted interests—often without your knowledge or consent.
A 2025 Privacy Rights Clearinghouse review identified over 500 active data broker sites operating in the U.S. alone. While some claim to use only “public data,” many purchase consumer records from retailers, apps, and marketing affiliates. The result: your personal information circulates among advertisers, insurers, and background-check firms indefinitely.
You can fight back by searching your name on major broker platforms and submitting opt-out requests. Some privacy services automate this, though persistence is key since listings often reappear.
Conclusion – Awareness Is the First Line of Defense
Information exposure is not a single event but a continual process. Social posts, corporate breaches, and smart-device data streams all contribute to an invisible web of personal information that others can analyze, sell, or exploit. But awareness, understanding where and how exposure occurs, is the first and most crucial line of defense.
You don’t need advanced technical skills to protect yourself. Simple actions, reviewing privacy settings, removing outdated data, and staying alert to breach notifications, can drastically reduce your digital footprint. When families treat privacy as a shared responsibility, they strengthen not only their data security but also their collective sense of calm and confidence.
Continue your learning with the main guide, Digital Identity Protection and PII Removal: Why It’s Now a Family Essential, which outlines a holistic approach to minimizing risk and reclaiming your digital privacy.
Ready to Secure Your Family's Future?
Join thousands of families who trust Proof of Life to manage their critical assets, documents, and legacy.
No Credit Card Required

